Crypto ID Based Networking
Networking Overview
Networking is all about locating and connecting to nodes. While Internet Protocol (IP) is the only option for connecting, there are currently three typical locating or “address book” architectures: Internet, P2P and SD-WAN. The “address book” for the network must be scalable, maintainable and secure.
Internet Protocol (IP)
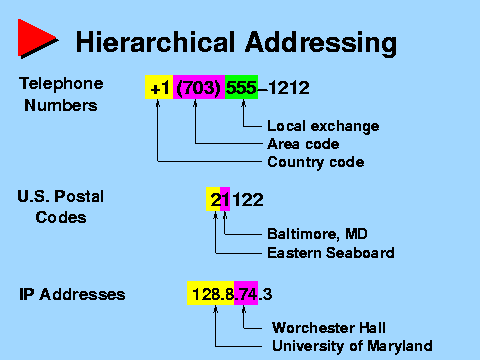
Internet uses IP addresses and relies on the Classless Inter-Domain Routing (CIDR) for allocating IP address and IP routing, and Border Gateway Protocol (BGP) to exchange routing information between Autonomous Systems (AS) Zones. The location information or the address-book is implicitly carried in the subnet mask or the hierarchical structure of each TCP/UDP packet. This architecture results in the dual roles of IP address and each IP address is tied to a hierarchical location.
P2P Network
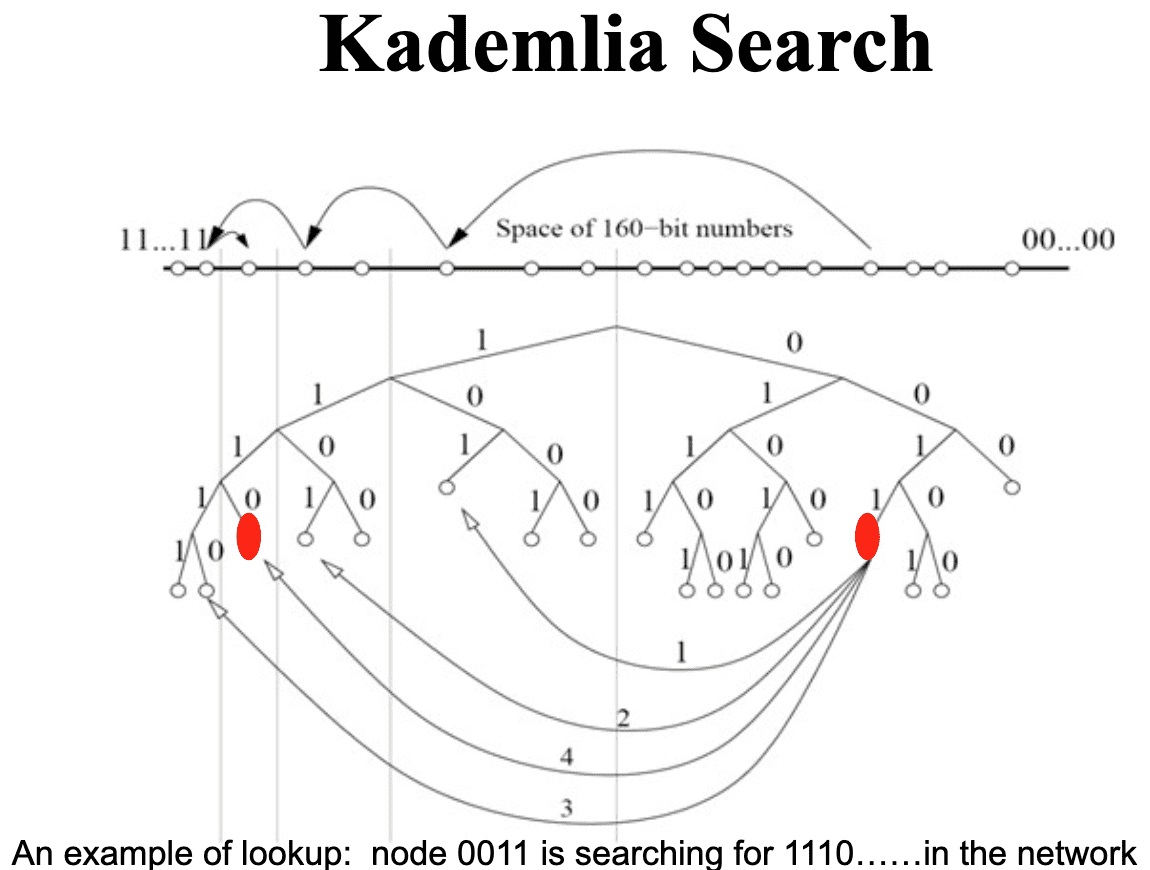
Typical P2P network use crypto-key XOR distance based location, commonly referring to Kademlia Distributed Hash Table (DHT), for the end-to-end connection between two nodes. The location information is implicitly carried in the crypto key and XOR distance. The XOR distance completely ignore the underlying IP hierarchical structure and may result in long latency between nodes.
Software-Defined WAN
Software-Defined WAN (SD-WAN) are used to programmatically create overlay network on top of the hierarchical IP topology to greatly improve flexibility and operational efficiency for enterprise, cloud platform and Telecom carriers. Corporate VPN is a common user case for SD-WAN. SD-WAN overlay network typically has central control plane and distributed data packet plane. The control plane maintains a central address book to explicitly map the node ID to physical IP address. The control plane also has a north-bound API for dynamically define the networking. SD-WAN’s scope is individual business.
Crypto ID Based Network
Each of the above networking architecture apparently has its own advantages, as well as limitations and is suited for different use case: Internet, P2P and distributed business respectively.
As contrast to the above three networking architectures, Đ.NETWORK is a new networking architecture, which is built upon P2P Blockchain platform:
- Explicitly maintain a decentralized crypto-key based addressing database for locating;
- Directive or pointer to connection brokers for connecting nodes and creating private networks over Internet;
- Programmatically define the network topology and firewall rules for securely control the access within the private network.
Đ.NETWORK combines and extends the openness of the Internet, programmability of SD-WAN and decentralized governance of P2P blockchain into a new networking architecture which supports fully autonomous, ubiquitous and encrypted connectivity.
